- Home >
- Stock Photos >
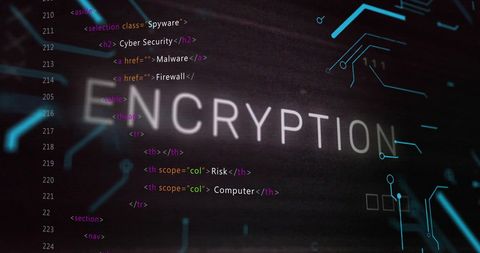
- Access Denied Computer Data Processing Cybersecurity Background
Access Denied Computer Data Processing Cybersecurity Background Image

Visual illustrating restricted access in a cybersecurity context. Ideal for materials on data protection, technology security protocols, and computer system protection guides. Suitable for blogs or newsletters discussing cyber threats, IT security strategies, or computer debugging scenarios.
downloads
Tags:
More
Credit Photo
If you would like to credit the Photo, here are some ways you can do so
Text Link
photo Link
<span class="text-link">
<span>
<a target="_blank" href=https://pikwizard.com/photo/access-denied-computer-data-processing-cybersecurity-background/07adc0e7b16589a942c66b4dc9f4eaf3/>PikWizard</a>
</span>
</span>
<span class="image-link">
<span
style="margin: 0 0 20px 0; display: inline-block; vertical-align: middle; width: 100%;"
>
<a
target="_blank"
href="https://pikwizard.com/photo/access-denied-computer-data-processing-cybersecurity-background/07adc0e7b16589a942c66b4dc9f4eaf3/"
style="text-decoration: none; font-size: 10px; margin: 0;"
>
<img src="https://pikwizard.com/pw/medium/07adc0e7b16589a942c66b4dc9f4eaf3.jpg" style="margin: 0; width: 100%;" alt="" />
<p style="font-size: 12px; margin: 0;">PikWizard</p>
</a>
</span>
</span>
Free (free of charge)
Free for personal and commercial use.
Author: Authentic Images