- Get 15% off with code: PIKWIZARD15
- Get 15% off with code: PIKWIZARD15- Home >
- Stock Photos >
- Hacker Coding with Digital Data Interface in Dark Environment
Hacker Coding with Digital Data Interface in Dark Environment Image

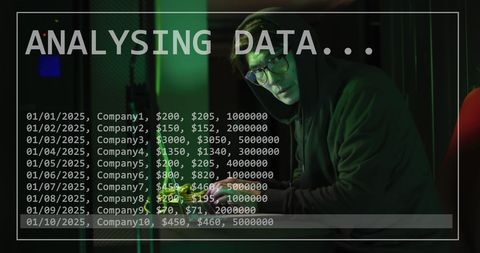
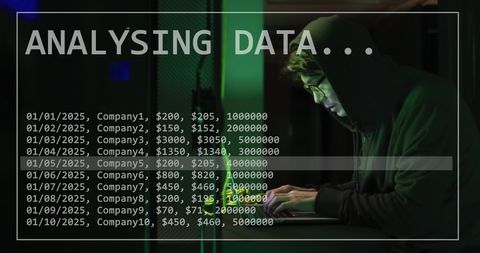
Hooded figure is surrounded by computer code and graphics, representing digital data processing in a secure environment. Reflecting concepts of cybercrime and technology, this image is ideal for use in cybersecurity articles, online security resources, or tech blogs and presentations discussing data protection and programming vulnerabilities.
downloads
Tags:
More
Credit Photo
If you would like to credit the Photo, here are some ways you can do so
Text Link
photo Link
<span class="text-link">
<span>
<a target="_blank" href=https://pikwizard.com/photo/hacker-coding-with-digital-data-interface-in-dark-environment/2fdc6d01e3da0643258821ab947dbcf2/>PikWizard</a>
</span>
</span>
<span class="image-link">
<span
style="margin: 0 0 20px 0; display: inline-block; vertical-align: middle; width: 100%;"
>
<a
target="_blank"
href="https://pikwizard.com/photo/hacker-coding-with-digital-data-interface-in-dark-environment/2fdc6d01e3da0643258821ab947dbcf2/"
style="text-decoration: none; font-size: 10px; margin: 0;"
>
<img src="https://pikwizard.com/pw/medium/2fdc6d01e3da0643258821ab947dbcf2.jpg" style="margin: 0; width: 100%;" alt="" />
<p style="font-size: 12px; margin: 0;">PikWizard</p>
</a>
</span>
</span>
Free (free of charge)
Free for personal and commercial use.
Author: Authentic Images