- Home >
- Stock Photos >
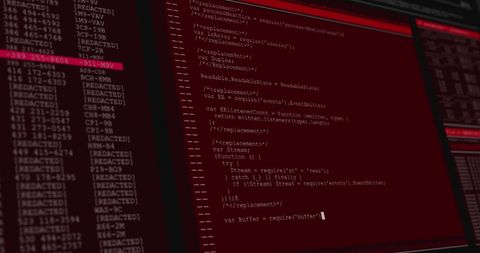
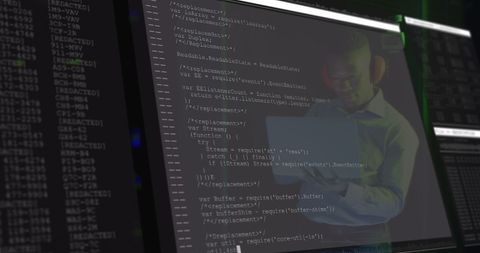
- Hacker in Action Through Overlayed Computer Code
Hacker in Action Through Overlayed Computer Code Image
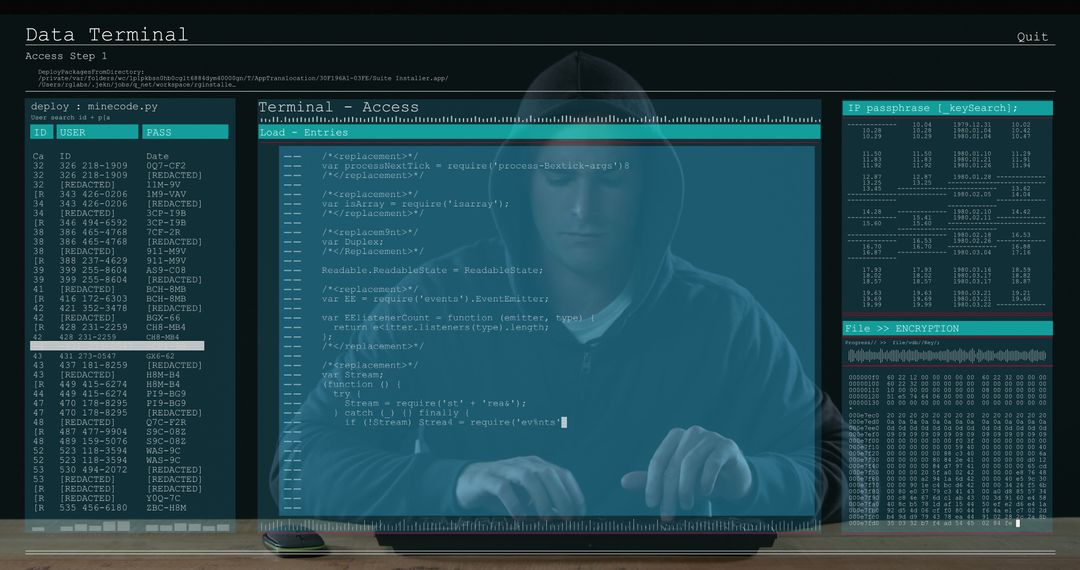
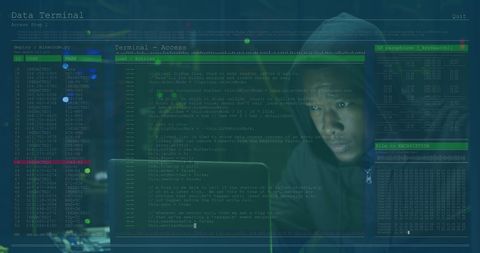
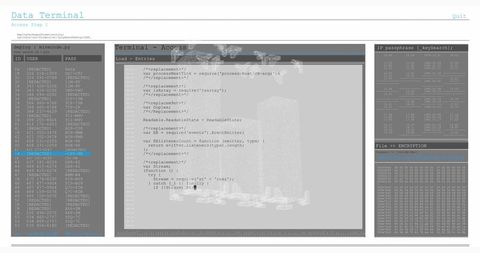
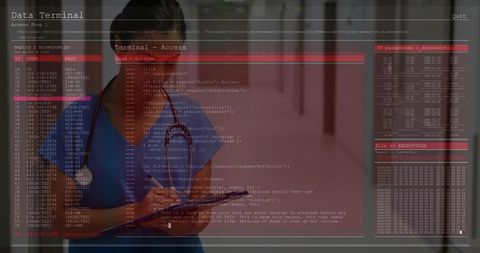
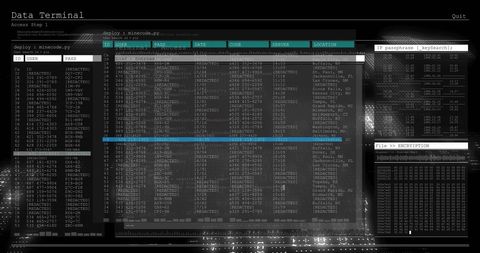
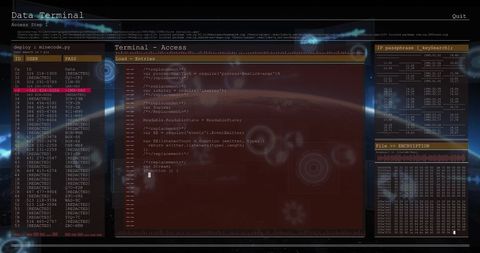
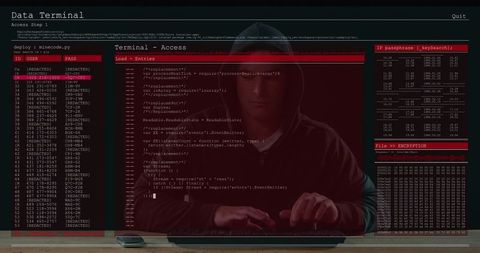
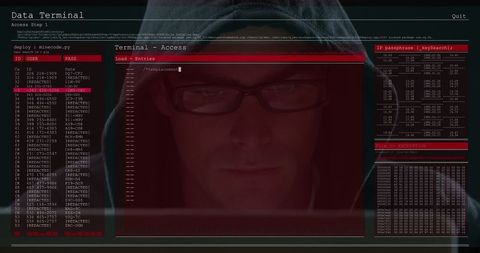
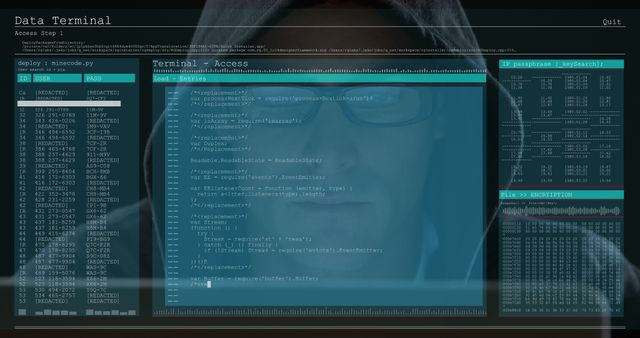
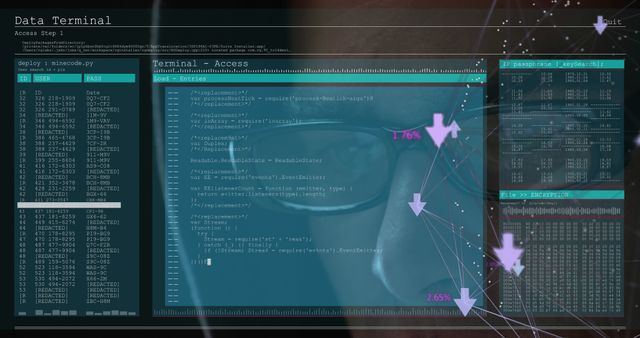
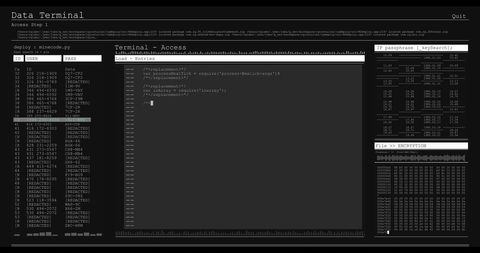
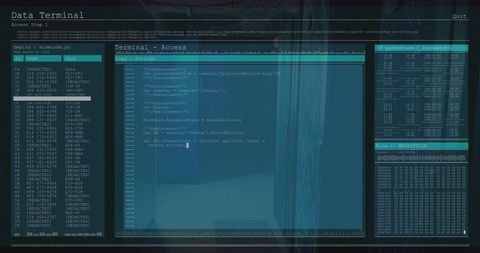
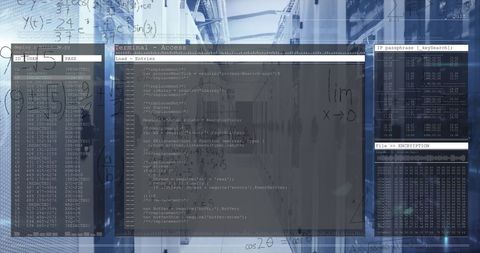
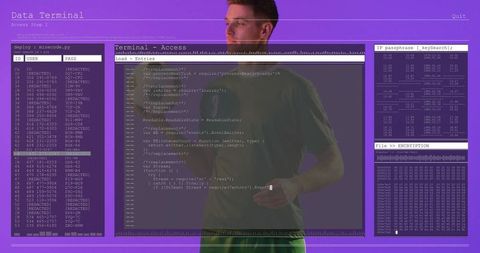
The visual represents a concept of cybersecurity and online threats, showing a male figure working on a computer with transparent computer code overlays. Useful for conveying themes of cybersecurity, hacking, digital forensics, and programming in blogs, articles, and educational materials.
downloads
Tags:
More
Credit Photo
If you would like to credit the Photo, here are some ways you can do so
Text Link
photo Link
<span class="text-link">
<span>
<a target="_blank" href=https://pikwizard.com/photo/hacker-in-action-through-overlayed-computer-code/dc56c34db51f57cc9e19d8474469cbf2/>PikWizard</a>
</span>
</span>
<span class="image-link">
<span
style="margin: 0 0 20px 0; display: inline-block; vertical-align: middle; width: 100%;"
>
<a
target="_blank"
href="https://pikwizard.com/photo/hacker-in-action-through-overlayed-computer-code/dc56c34db51f57cc9e19d8474469cbf2/"
style="text-decoration: none; font-size: 10px; margin: 0;"
>
<img src="https://pikwizard.com/pw/medium/dc56c34db51f57cc9e19d8474469cbf2.jpg" style="margin: 0; width: 100%;" alt="" />
<p style="font-size: 12px; margin: 0;">PikWizard</p>
</a>
</span>
</span>
Free (free of charge)
Free for personal and commercial use.
Author: Creative Art